Ad Drozek Malware
Extensive malware campaigns affect multiple browsers trying to quietly inject ads into search results
RAM Research Team – Ad Drozek
Since at least May 2020, a permanent malware campaign has been actively distributing new methods and malware to more and more advanced browser modifiers. At the peak of August, the threat was being carried out on 3,000,000 devices every day. Malware is designed to inject information or ads into search engine results pages. Microsoft Edge, Google Chrome, Yandex Browser, and Mozilla Firefox – many of the browsers exposed by the attackers aim to reach the maximum number of Internet users are at risk of this threat.
We refer to this family of browser modifiers as Ad Drozek. If detected and not blocked, Ad drojek is a browser extension, modifying the specific DLL for each target browser, and modifying browser settings to include additional, unauthorized ads on web pages, often valid from search engines. Are. Intended effect For users, looking for specific keywords, inadvertently clicking on these malware-included ads, which leads to relevant pages. Aggressive advertising is the act of making money through philatelic advertising diversion programs, which pay for the amount of traffic referenced on sponsored affiliate pages.
Figure 1. Comparison of search results pages on the affected machine and Adroject running pages.
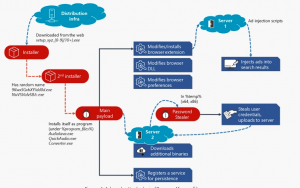
Frequent misuse of affiliate programs is not new to cybercriminals – these browser modifiers continue to be some of the oldest threats. However, the fact that these campaigns use a piece of malware that affects multiple or multiple browsers serves to demonstrate how this type of threat is becoming more sophisticated and widespread. Also, the malware persists and exposes the additional risk to the affected website and makes it clear.
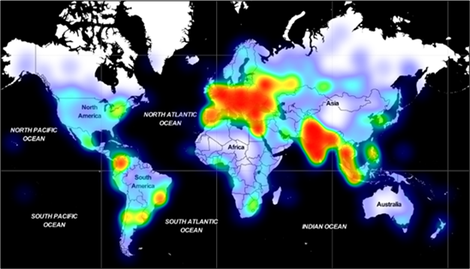
Such a continuous and recurring, far-reaching mission requires a wide range of dynamic attack infrastructure or concrete facilities. We tracked 19 unique domains, each hosting an average of 1,300 unique URLs, typically hosting over 1,300 different, polymorphic malware types. Overall, from May to September 2020, we have investigated millions of encounters with androgenic malware worldwide, with large and maximum concentrations in Europe and South Asia, and Southeast Asia. As the campaign continues, the infrastructure is set to expand further.
Figure 2. Geographical distribution of androgens encounters from May to September 2020.
To effectively protect against such a relentless, persistent campaign that involves multiple and multiple elements, polymorphism, different and evolving malware behaviors, requires advanced, behavior-based detection as well as visibility across the entire attack chain rather than different elements. Microsoft Defender antivirus, the built-in endpoint protection solution on Windows 10, uses this behavior-based, machine learning-supported protection to make this threat or accident happen. For ventures, the Microsoft 365 Defender provides deep visibility into malicious behavior. In this blog, we’ll share an in-depth analysis of this campaign, along with distribution architecture and malware behavior, and provide information on recommended protection.
References:
- https://www.microsoft.com/security/blog/2020/12/10/widespread-malware-campaign-seeks-to-silently-inject-ads-into-search-results-affects-multiple-browsers/
- https://www.zdnet.com/article/microsoft-exposes-adrozek-malware-that-hijacks-chrome-edge-and-firefox/
- Cyber Swachhta Kendra – Security Tools Section






