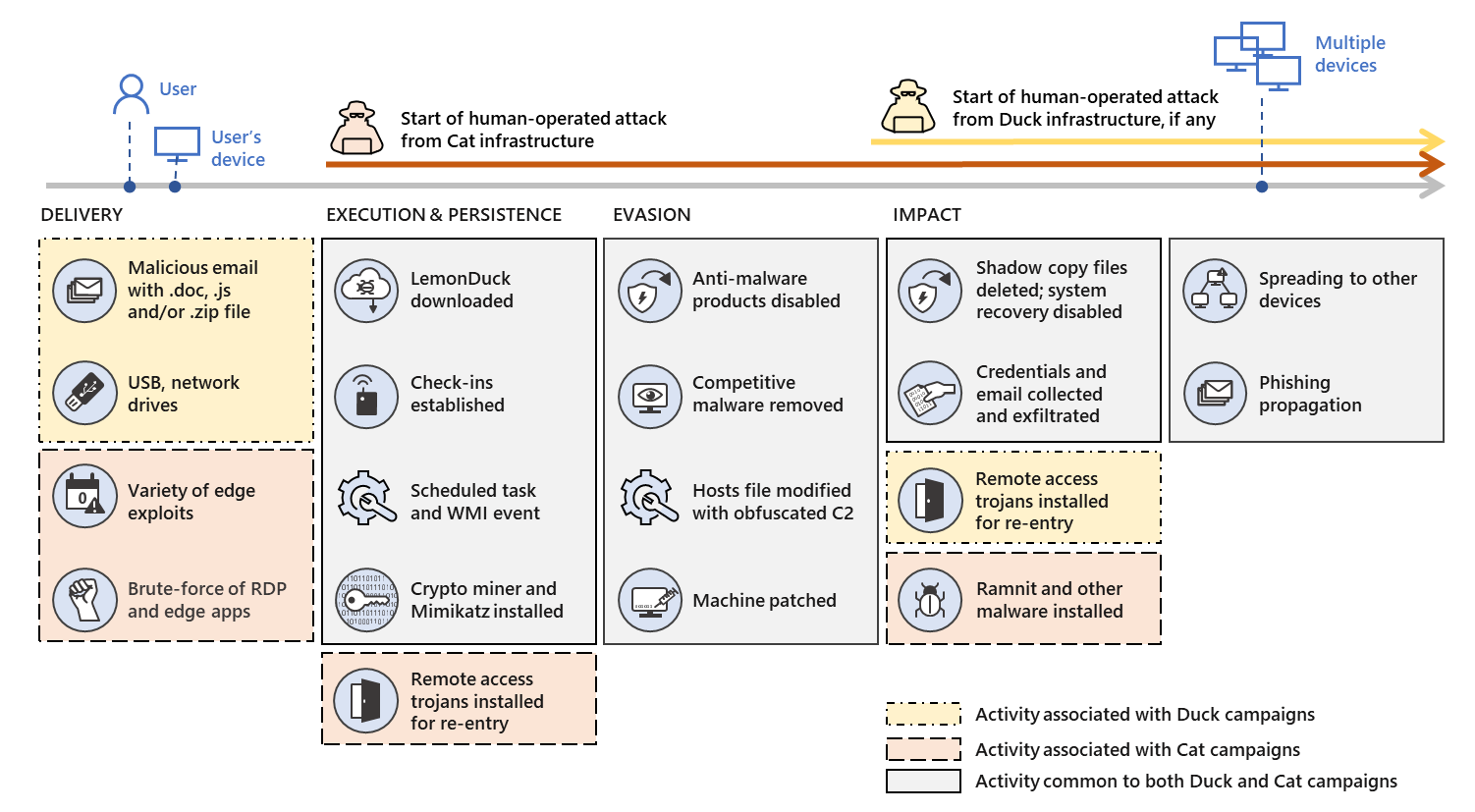
An infamous crypto mining malware that was highlighted a few years ago is on the rise again, targeting Windows PCs (and Linux as well) by focusing on older vulnerabilities that may no longer be doing so. subject to a thorough investigation by the security community. Referred to as LemonDuck, the growing threat LemonDuck became highly sophisticated malware – and is used today by threat actors to target companies with vulnerabilities. old and uncorrected in their system.
Once targeted, the consequences can be disastrous. According to Microsoft, LemonDuck’s capabilities include stealing key credentials from Windows and Linux PCs, removing security checks to render system administrators powerless, emailing (possibly spear phishing attempts) and installation in systems to allow additional remote code execution (RCE)) backdoors – something that can therefore leave computers completely open to an endless number of ransomwares, spyware or other sophisticated tools from cyber warfare.
Highlighting how critical and pervasive the threat of LemonDuck can be, reported that it can quickly take advantage of news, events, or the publication of new exploits to run effective campaigns. For example, in 2020 it was observed to use Covid-19-themed decoys in email attacks. In 2021, he exploited recently patched Exchange Server vulnerabilities to gain access to obsolete systems. “
The top two malware known for botnet and crypto mining attacks are not near the end of the list of tools that can launch catastrophic cyber-attacks against key companies in key industries. Older systems are one of the primary ways in which these attacks spread, so users and IT administrators can quickly fix many vulnerabilities in systems that may be exposed to serious threats. And immediate updates are essential.
How did it work?
The infection starts with a PowerShell load script, which is copied from other infected systems with SMB, email, or external USB drives. The actor also uses several exploits for vulnerabilities such as SMBGhost and Eternal Blue. The code exploiting the Bluekeep vulnerability is also present but it is disabled in the version we analyzed.
The botnet has executable modules that are downloaded and driven by the main module, which communicates with the command and control (C2) server via HTTP.
The email delivery module uses subject lines and text related to COVID-19, with an infected attachment sent using Outlook Automation to every contact in the company’s address book. affected user.
Lemon Duck malware
Recently discovered that advanced crypto-miner malware Lemon Duck added the ProxyLogon exploit to one of its updates. This updated version was used to target unpatched Microsoft Exchange servers, along with a range of features that, between them, allow the malware to take a firm hold in a compromised server, while escaping detection by the defenders.
Attacks using the ProxyLogon exploit involve the injection of web shells on an infected server. These web shells are attacker files that are added to a web server directory and allow the attacker to issue new instructions, for example to execute a file at any time simply by requesting it from the web server.
Web shells are pernicious. They provide attackers with a permanent backdoor to a victim’s web applications and associated systems, with the ability to add commands of their choice, whenever they want, directly to the web server, without needing to log in beforehand.
This version of Lemon Duck allows an attacker to copy the web shells they are using and hide them in a different location, increasing the likelihood that the shells will remain invisible so that they can be reused.
However, this is not the only characteristic of a Lemon Duck attack activated by ProxyLogon. Others include:
- Installing the miner’s payload as a Windows service to establish persistence
- Using an Oracle WebLogic server exploit used to attempt to move sideways to other servers on the network
- In some cases, using certutil.exe to download the Lemon Duck payload, which is launched using PowerShell
- Creating a user account with remote desktop access
- Updates to the Lemon Duck Defense Escape Code, which attempt to disable and remove even more security products.
Capabilities of LemonDuck
- Exploit
- Information Theft
- Persistence
Impact of LemonDuck
- Exfiltration Over Command-and-Control Channel
- Resource Hijacking
What LemonDuck malware does and things users must be aware of:
Today, beyond using resources for its traditional bot and mining activities, LemonDuck steals credentials, removes security checks, spreads via email, travels around laterally and ultimately remove more tools for human activities, “Microsoft explained in the blog, adding that countries like the US, Russia, China, Germany, UK, India, Korea, Canada, France and Vietnam have seen the most infections so far.







Leave A Comment