Sophisticated Malware Hidden in Imitation Palo Alto Tool
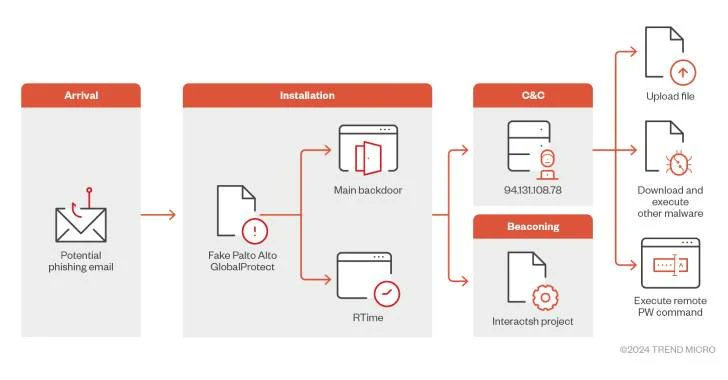
There is a really serious threat going around, this new advanced malware. That aims at organizations in the Middle East. It is hiding as a valid Palo Alto GlobalProtect. So an advanced C&C infrastructure is a two-step infection process
It uses the Interactsh project for Beacoming and C2 and utilizes it to run remote PowerShell commands, download and upload files, and get around sandbox solutions.
It can hold a permanent connection through a fake VPN entry point. So it’s that kind of power that makes it such a serious threat in the world of cybersecurity.
Introduction of the Fake Palo Alto Tool
In the global threat landscape of cybercrime perception, infringers are going to creative efforts so, as not to wait for somebody to space and then to continue the unlawful act. However, among the rather cupping techniques of recent times. There is scam-hosted cybersecurity software produced in the wrong hands and claiming products of authorized entities.
For instance, it was the news about the discovery of a bogus Palo Alto Networks product that was thought to be the right solution but in reality, it was just a scam aimed at users to unwitting performance. Consequently, this phony app is indeed a protective feature that has been hidden cleverly; it can end up being the mask.
How it works:
Infection: Malware infects a system. Through phishing, downloads, or vulnerabilities.
Execution: After being inside the system, If it becomes active and starts. Then execute malicious code.
Propagation: Malware replicates to other systems and infects as much as possible.
Damage: It performs malicious actions against the system. Then it steals data, encrypts files for ransom, spies on users, or disrupts system operation.
Effects of Malware:
Data Theft: Malware can steal passwords Not only financial information But Also personal files. And other sensitive information.
Financial Loss: These include huge financial damages. In the form of ransom, fraud, and downtime. ·
System Damage: The malware may corrupt or destroy certain files. So making systems inoperable. ·
Network Disruption: Some malware spreads across networks. And bring organizations to a standstill with citywide downtowns.
Timeline of the recent attack on this Fake Palo Alto Tool Delivering Sophisticated Malware
Initial Exposure (August 2024): This malware campaign was first discovered at the end of August 2024. So The attackers began spreading the setup file, setup.exe. And Masquerading as a setup installer of Palo Alto GlobalProtect VPN. Then The fake installer probably spread via phishing emails or compromised websites.
Targeting and Impact: The attack was very focused, with the organizations under attack located within the Middle East, in sectors of strategic importance. The very fact that a VPN tool was used as the bait in this case suggests the level of sophistication in understanding regional infrastructure and possible geopolitical motives
Prevention measures: include the following.
Only Download from Official Sources: Applications, or any other kind of software. Then download only from the official website of Palo Alto Networks or an authorized reseller.
Verify Authenticity, Check Digital Signatures: Software must have a valid digital signature from Palo Alto Networks. This is usually verified from the properties of the file.
Educate and Train: Impart regular training to employees regarding phishing, social engineering, and safe software practices. Make them aware of identifying legitimate sources and how to avoid downloading software from suspicious links.
Employ Multi-Factor Authentication: Impose MFA on sensitive systems and tools. This again raises the bar of security so that the chances of attack without authorization become very hard to manage by an attacker.
Network Security Controls, Firewalls: Provide firewalls and then configure them for prevention against unauthorized access and other forms of attacks.
Monitoring and auditing: The policy provides for the periodic review and monitoring of systems. and network logs for suspicious activity. This ensures that any potential compromises.
Backup Data: Provide regular backups of critical data and systems. Then the backups are stored and restored quickly in case of malware infection.
How RAM Antivirus Helps in:
Real-time Scanning: Antivirus solutions continuously scan the memory of a system. And any malicious process or code. So Advanced malware resides in memory as one of the evasion techniques. Real-time scanning helps to identify and block active threats.
Heuristic Detection: This technique will analyze the behavior and characteristics of programs to determine possible threats that do not match the signature characteristics of known viruses. It could be able to detect sophisticated malware masquerading itself as a legitimate tool of Palo Alto through heuristic analysis by finding patterns typical for malware.
Memory Protection Against Exploits: Most malware exploits vulnerabilities in software to execute malicious code in memory. So Antivirus solutions that have good memory protection block such exploits before the malware compromises the system.
Alerts and Reporting: It is suspicious activities. Because a fake Palo Alto tool is detecting. And the antivirus flags this for your immediate attention. So take remedial action before the malware causes damage.
To download RAM Antivirus:
Visit the official website, https://ramantivirus.in/ select the version compatible with your operating system, search for the antivirus you want, and click the “Download” button. Once the file downloads. please open it and follow the instructions to complete the installation. After installation, launch RAM Antivirus to begin protecting And Securing your device.











Leave A Comment